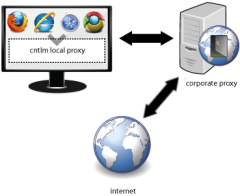
 While a lot of applications allow you to configure proxy settings, quite a few do not support NTLM authentication. Unfortunately, a lot of corporate proxies use NTLM to authenticate their users. To get around this, we can use a free utility called Cntlm to connect these applications to the corporate network. For this example, we will be using Dropbox (referral link) and Trillian, but once configured it should work with any application that allows you to set proxy settings manually. These instructions are for Windows, but Linux builds are available on their Sourceforge page and Mac users can use Authoxy.
While a lot of applications allow you to configure proxy settings, quite a few do not support NTLM authentication. Unfortunately, a lot of corporate proxies use NTLM to authenticate their users. To get around this, we can use a free utility called Cntlm to connect these applications to the corporate network. For this example, we will be using Dropbox (referral link) and Trillian, but once configured it should work with any application that allows you to set proxy settings manually. These instructions are for Windows, but Linux builds are available on their Sourceforge page and Mac users can use Authoxy.
NOTE: If the port number used by the application is blocked on the proxy, Cntlm won’t be able to get around this. You may also not be able to do this if your account is locked down to prevent installations – see the end of this post for one way around this.
What You’ll Need
- Cntlm, a utility which stands between your applications and the corporate proxy, adding NTLM authentication on-the-fly.
- Windows XP or newer: Linux builds of Cntlm are available on their Sourceforge page and Mac users can use Authoxy, but I will not be showing you how to configure these.
- At least one application to test the configuration. I’m going to use Dropbox and Trillian, but you can also try it with whichever application you are attempting to run.
Step One: Installing Cntlm
Download the latest version of Cntlm (0.92.3 at the time of writing). Run through the installer clicking Next, making sure to accept the license agreement and to note down the installation folder. Once the installer has completed, navigate to the installation folder.
Step Two: Configuring Cntlm
Before doing anything else, make a backup of cntlm.ini – if anything goes wrong we can simply revert to this backup and start again.
Configure the proxy address
Now look for the following section:
# List of parent proxies to use. More proxies can be defined
# one per line in format <proxy_ip>:<proxy_port>
#
Proxy 10.0.0.41:8080
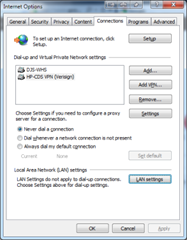
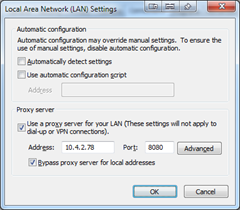
Proxy 10.0.0.42:8080Remove the second Proxy line, then replace the IP address and port with your proxy settings (you can usually find these by opening Internet Explorer, then clicking Tools –> Internet Options –> Connections –> LAN Settings.
Configure the username and domain
Now we have the proxy address configured, we can configure the username and password. Look for the following section:
Username testuser
Domain corp-uk
Password password
# NOTE: Use plaintext password only at your own risk
# Use hashes instead. You can use a "cntlm -M" and "cntlm -H"
# command sequence to get the right config for your environment.
# See cntlm man page
# Example secure config shown below.
# PassLM 1AD35398BE6565DDB5C4EF70C0593492
# PassNT 77B9081511704EE852F94227CF48A793
### Only for user 'testuser', domain 'corp-uk'
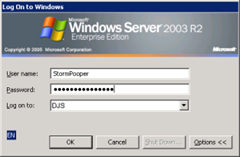
# PassNTLMv2 D5826E9C665C37C80B53397D5C07BBCBFirst, we replace the username and domain with your login credentials. In most companies, this will be the same as your login details for the computer. For example, to login, you may have to enter DJS\StormPooper. In this example, DJS is the domain and StormPooper is the username. If you do not enter your login details like this, then when you are next logging into a work computer, the domain name will be shown on the logon screen as Log on to (you may have to click Advanced to see this). Once you have done this, save your changes, but keep the file open.
Configure the password
Now we need to store your password. As the comment in the configuration file suggests, storing your password as plain text (just typing it in) is a terrible idea, as anyone with access to the system can see your password. To store the password securely, we have to generate a hash of the password. Luckily, Cntlm includes tools to do this. Open a command line (Start –> Run –> cmd) and navigate to the installation directory (on my system, for example, I enter cd "C:\Program Files (x86)\Cntlm" since I’m running a 64-bit version of Windows).
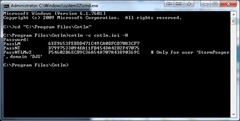
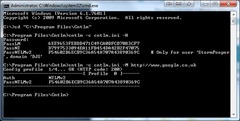
Now we need to generate the hash. Enter this in the command line:
cntlm –c cntlm.ini –H
You should see 3 hashes as per the screenshot above. Copy these and paste them into cntlm.ini, uncommenting the 3 Pass lines and making sure you comment out the Password field. The final results should look like this:
Username StormPooper
Domain DJS
# Password password
# NOTE: Use plaintext password only at your own risk
# Use hashes instead. You can use a "cntlm -M" and "cntlm -H"
# command sequence to get the right config for your environment.
# See cntlm man page
# Example secure config shown below.
PassLM 1AD35398BE6565DDB5C4EF70C0593492
PassNT 77B9081511704EE852F94227CF48A793
### Only for user 'StormPooper', domain 'DJS'
PassNTLMv2 D5826E9C665C37C80B53397D5C07BBCBOnce you have entered your hashes, save your changes. Then in the command line, enter the following command to determine if the settings work:
cntlm –c cntlm.ini –I –M http://www.google.co.uk
If you see something similar to above, you have successfully configured Cntlm. If not, double-check your hashes are correct and your proxy settings.
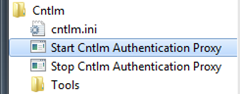
Starting the service
Now that the configuration file is complete, we have to start Cntlm’s proxy service. Click on Start –> All Programs –> Cntlm –> Start Cntlm Authentication Proxy to start the service.
If you ever need to change the configuration, click Stop Cntlm Authentication Proxy before making any changes, then restart the service to test your changes.
Step Three: Using the proxy with applications
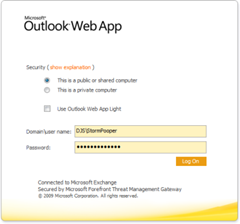
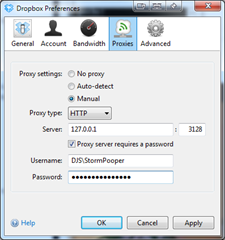
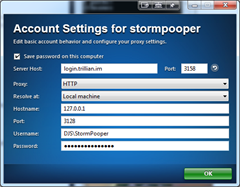
Now to test your configuration. Note that each application is different with regards to proxy settings, but the settings you need to enter will be the same for all of them. Basically, we have to manually configure the proxy to use HTTP and point it to 127.0.0.1, with the port number 3128 (you can change this port number in the configuration file if needed). If there is a place to, enter your username and password in the same way as before – see the two screenshots below for examples.
Once you apply these settings, you should be able to connect using the applications in question.
Conclusion and Advanced Configuration
Now you should be able to run most applications that need to going through the proxy. If you have any difficulties, you should restore the backup you made and start again from step two. If you need to use advanced features such as SOCKS5, you can also configure these using the configuration file – more information about advanced configuration can be found on their Help Forums. If you are unable to install Cntlm, you can download the zip file version and create a service using the following command (note the spaces between = and “), though this will still need permissions to create a service:
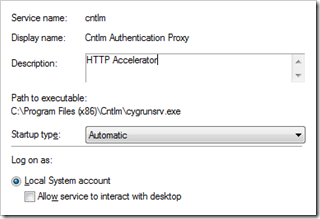
sc.exe create cntlm binPath= "C:\Program Files (x86)\Cntlm\cygrunsrv.exe" DisplayName= "Cntlm Authentication Proxy"
If you click Start –> Run –> services.msc and double-click the service settings, they will be similar to below (note that Log on As is on the next tab).
If the application you are attempting to run does not let you specify a proxy manually, the likelihood is that it is automatically reading Internet Explorer’s proxy configuration. To bypass this, you can point Internet Explorer to Cntlm in the LAN Settings. Note that on most corporate machines, proxy settings are automatically configured, so your changes may be erased – configuring each application manually avoids this issue.
If all of this manual configuration makes you want to stab your computer in the throat, you can buy Proxifier – it comes with a 31 day trial, so see if this works for you. Alternatively, leave a comment below or use the contact form and I will happily try and work through any issues you may be having.

 Subscribe with iTunes
Subscribe with iTunes